- 0 Posts
- 81 Comments
I’m partial to this representation:

Isn’t your example just the builder pattern?
The exact same thing happened to me, just a little differently. When I accepted the offer, the system automatically removed me from the other application and sent a generic rejection email. Scared the shit out of me.
I believe any smooth piece of metal without any gaps or sharp edges (so no forks or foil) is fine in a microwave.
That might be good for shortlinking

 203·3 months ago
203·3 months agoA little further down:
In popular usage, the word pedophilia is often applied to any sexual interest in children or the act of child sexual abuse, including any sexual interest in minors below the local age of consent or age of adulthood, regardless of their level of physical or mental development.
But those are way more useful than vibe coding.
Try to automate part of your tedious work. You may spend more time automating a task than doing it manually, but that’s where the fun is.

 8·6 months ago
8·6 months agoTbf, old comments can also give important context through earlier refactors and help avoid treading the same ground again.
That being said, this is with the assumption that the next dev making a change will add their own comments describing it.
Having never used it before, is it that bad?
Measuring a coastline creates a well known paradox: https://en.m.wikipedia.org/wiki/Coastline_paradox

 2·6 months ago
2·6 months agoTIL
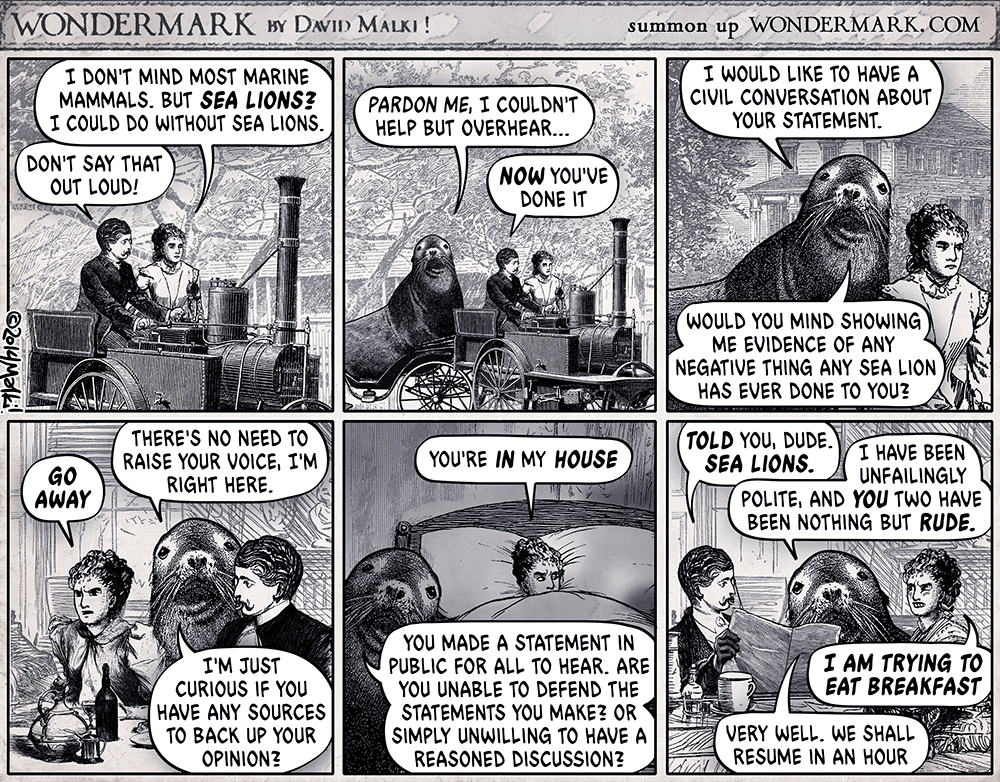
Sealioning (also sea-lioning and sea lioning) is a type of trolling or harassment that consists of pursuing people with relentless requests for evidence, often tangential or previously addressed, while maintaining a pretense of civility and sincerity (“I’m just trying to have a debate”), and feigning ignorance of the subject matter. It may take the form of “incessant, bad-faith invitations to engage in debate”, and has been likened to a denial-of-service attack targeted at human beings. The term originated with a 2014 strip of the webcomic Wondermark by David Malki, which The Independent called “the most apt description of Twitter you’ll ever see”.
Yugi when the opponent is doing a little too well
But python lists are not like the base arrays in other languages. They function more like
List<>orvector(C++ had to be special) and are named appropriately.
The problem with recreating cryptographic libraries is that unless you are a cybersecurity expert, you are very likely to leave hidden vulnerabilities in your implementation.






Here we see, another innocent victim being drawn into the addictive clutches of Cracktorio. The factory must grow.